Tips for Overcoming Barriers to a Smooth BYOD Program
Bring your own device (BYOD) is a concept that took hold after the invention of the smartphone. When phones got smarter, software developers began...
2 min read
JPtheGeek May 29, 2024 2:56:00 PM
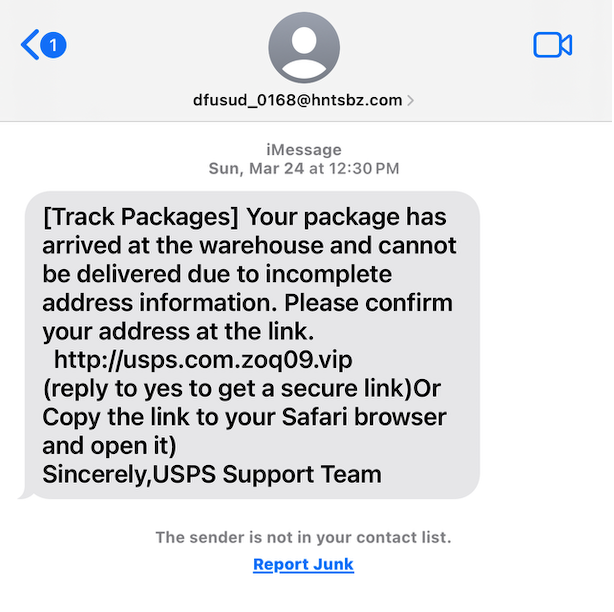
In an age where our smartphones rarely leave our sides, smishing—SMS phishing—has emerged as a prevalent cybersecurity threat. Smishing attacks leverage text messages to deceive recipients into divulging sensitive information. Here's what you need to know about smishing and how to safeguard against it.
Smishing is a form of phishing that comes via SMS, the text messaging service on your mobile phone. It's a crafty technique that cybercriminals use to extract personal details such as passwords, bank account numbers, or Social Security numbers. Smishing messages often mimic urgent communications from banks, sweepstakes, tech companies, or delivery services, exploiting the trust and urgency we associate with these entities.
Fake Bank Alerts: These messages prey on your financial security fears, claiming your account has seen suspicious activity. They prompt you to click a link to “resolve” the issue—a classic smish.
Winner Notifications: These texts congratulate you on winning a contest you never entered, asking you to click a link or send personal details to claim the prize.
Password Reset Requests: Purportedly from tech giants like Google or Microsoft, these smishing attempts alert you to a security breach, urging you to click a link to reset your password.
Package Delivery Updates: Smishers may impersonate e-commerce platforms, informing you about a package delivery and providing a link to update delivery preferences.
Confirmation Requests: Messages asking you to confirm a parcel, appointment, or payment, typically directing you to a fraudulent website to collect your information.
Here’s how you can protect yourself and your business from smishing:
Skepticism is Key: Treat unsolicited texts with suspicion, especially those requesting personal information or action via a link.
No Links, Please: Legitimate organizations rarely ask for sensitive information or instruct you to follow a link via text. When in doubt, contact the organization directly using a verified phone number or website.
Stay Informed: Keep up to date on the latest smishing tactics to recognize them quickly.
Check the Source: Look for tell-tale signs of smishing, like misspelled words, strange URLs, and messages that create a sense of urgency.
Use Technology Wisely: Employ spam filters on your phone and report smishing attempts to your service provider.
Educate Others: Share information about smishing with your network. Awareness is one of the best defenses against smishing.
Smishing is an insidious threat in our digital world, but with vigilance and education, we can reduce its impact. By understanding the forms smishing takes and how to respond appropriately, you can protect yourself from these deceptive tactics. Remember, when it comes to unsolicited texts asking for personal information, it's better to be safe than sorry. Always verify the source, and never click on suspicious links. Stay safe and stay informed.

Bring your own device (BYOD) is a concept that took hold after the invention of the smartphone. When phones got smarter, software developers began...

For small businesses, the prospect of investing in cybersecurity can sometimes seem daunting, especially with tight budgets and limited resources....

Why Small Businesses Need Managed IT Services More Than Ever